What Is the Probability That the Correct Source Element Can Be Selected by an Adversary on One Try?
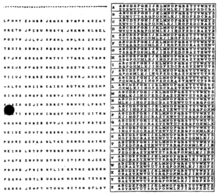
A format of one-time pad used by the U.South. National Security Agency, code named DIANA. The table on the correct is an aid for converting between plaintext and ciphertext using the characters at left every bit the key.
In cryptography, the sometime pad (OTP) is an encryption technique that cannot exist cracked, simply requires the use of a single-utilize pre-shared key that is no smaller than the bulletin beingness sent. In this technique, a plaintext is paired with a random secret key (besides referred to every bit a old pad). And so, each bit or grapheme of the plaintext is encrypted by combining it with the respective bit or character from the pad using modular addition.
The resulting ciphertext will be impossible to decrypt or break if the post-obit four conditions are met:[i] [2]
- The fundamental must be at to the lowest degree equally long as the plaintext.
- The cardinal must exist random (uniformly distributed in the set of all possible keys and independent of the plaintext), entirely sampled from a non-algorithmic, chaotic source such as a hardware random number generator. It is not sufficient for OTP keys to pass statistical randomness tests as such tests cannot measure entropy, and the number of bits of entropy must exist at least equal to the number of bits in the plaintext. For case, using cryptographic hashes or mathematical functions (such as logarithm or square root) to generate keys from fewer bits of entropy would intermission the uniform distribution requirement, and therefore would not provide perfect secrecy.
- The fundamental must never be reused in whole or in role.
- The key must be kept completely clandestine by the communicating parties.
It has also been mathematically proven that whatever nothing with the property of perfect secrecy must apply keys with effectively the same requirements as OTP keys.[3] Digital versions of one-fourth dimension pad ciphers have been used past nations for critical diplomatic and armed forces communication, just the problems of secure key distribution make them impractical for most applications.
Starting time described by Frank Miller in 1882,[4] [5] the onetime pad was re-invented in 1917. On July 22, 1919, U.Due south. Patent 1,310,719 was issued to Gilbert Vernam for the XOR operation used for the encryption of a one-time pad.[6] Derived from his Vernam zero, the system was a cipher that combined a bulletin with a key read from a punched tape. In its original form, Vernam'south organization was vulnerable because the cardinal tape was a loop, which was reused whenever the loop made a full cycle. Old use came subsequently, when Joseph Mauborgne recognized that if the fundamental tape were totally random, then cryptanalysis would be impossible.[seven]
The "pad" part of the proper name comes from early implementations where the key material was distributed equally a pad of newspaper, allowing the electric current top sheet to exist torn off and destroyed afterward use. For concealment the pad was sometimes so small that a powerful magnifying glass was required to use it. The KGB used pads of such size that they could fit in the palm of a hand,[viii] or in a walnut shell.[9] To increase security, sometime pads were sometimes printed onto sheets of highly flammable nitrocellulose, so that they could hands be burned later use.
At that place is some ambiguity to the term "Vernam cipher" because some sources use "Vernam null" and "one-fourth dimension pad" synonymously, while others refer to whatever condiment stream cipher as a "Vernam zilch", including those based on a cryptographically secure pseudorandom number generator (CSPRNG).[10]
History [edit]
Frank Miller in 1882 was the get-go to describe the onetime pad system for securing telegraphy.[five] [xi]
The next one-time pad system was electrical. In 1917, Gilbert Vernam (of AT&T Corporation) invented[12] and later patented in 1919 (U.S. Patent one,310,719) a cipher based on teleprinter technology. Each character in a message was electrically combined with a character on a punched newspaper tape key. Joseph Mauborgne (then a captain in the U.S. Army and subsequently chief of the Signal Corps) recognized that the graphic symbol sequence on the primal record could be completely random and that, if then, cryptanalysis would be more difficult. Together they invented the get-go one-time tape arrangement.[10]
The adjacent evolution was the paper pad organization. Diplomats had long used codes and ciphers for confidentiality and to minimize telegraph costs. For the codes, words and phrases were converted to groups of numbers (typically 4 or v digits) using a dictionary-like codebook. For added security, secret numbers could be combined with (usually modular add-on) each code group before manual, with the secret numbers being changed periodically (this was chosen superencryption). In the early 1920s, three German cryptographers (Werner Kunze, Rudolf Schauffler, and Erich Langlotz), who were involved in breaking such systems, realized that they could never be cleaved if a dissever randomly called additive number was used for every lawmaking grouping. They had duplicate paper pads printed with lines of random number groups. Each page had a serial number and eight lines. Each line had six 5-digit numbers. A folio would be used every bit a piece of work canvass to encode a message so destroyed. The serial number of the page would be sent with the encoded message. The recipient would opposite the procedure so destroy his copy of the page. The German foreign office put this organisation into operation by 1923.[10]
A separate notion was the employ of a one-time pad of messages to encode plaintext directly as in the example below. Leo Marks describes inventing such a organisation for the British Special Operations Executive during World State of war Ii, though he suspected at the fourth dimension that it was already known in the highly compartmentalized globe of cryptography, equally for instance at Bletchley Park.[13]
The concluding discovery was fabricated past data theorist Claude Shannon in the 1940s who recognized and proved the theoretical significance of the quondam pad organization. Shannon delivered his results in a classified written report in 1945 and published them openly in 1949.[3] At the same time, Soviet data theorist Vladimir Kotelnikov had independently proved the absolute security of the i-fourth dimension pad; his results were delivered in 1941 in a report that manifestly remains classified.[fourteen]
Example [edit]
Suppose Alice wishes to send the message hi to Bob. Assume two pads of newspaper containing identical random sequences of letters were somehow previously produced and securely issued to both. Alice chooses the appropriate unused page from the pad. The way to do this is normally arranged for in advance, equally for instance "use the 12th canvass on 1 May", or "use the side by side bachelor canvass for the side by side message".
The fabric on the selected sheet is the key for this message. Each alphabetic character from the pad will be combined in a predetermined fashion with 1 letter of the bulletin. (It is common, but not required, to assign each letter a numerical value, eastward.g., a is 0, b is 1, and and so on.)
In this example, the technique is to combine the primal and the bulletin using modular addition (essentially the standard Vigenère zero). The numerical values of corresponding bulletin and key letters are added together, modulo 26. And then, if key textile begins with XMCKL and the message is hello, then the coding would be washed as follows:
h e l l o message vii (h) four (e) 11 (l) 11 (l) fourteen (o) message + 23 (X) 12 (M) 2 (C) 10 (K) xi (L) key = 30 16 13 21 25 message + cardinal = iv (Due east) xvi (Q) xiii (N) 21 (V) 25 (Z) (bulletin + key) mod 26 East Q Due north V Z → ciphertext
If a number is larger than 25, and then the residual afterward subtraction of 26 is taken in modular arithmetic fashion. This only means that if the computations "go past" Z, the sequence starts again at A.
The ciphertext to exist sent to Bob is thus EQNVZ. Bob uses the matching key page and the same process, but in reverse, to obtain the plaintext. Here the central is subtracted from the ciphertext, once again using modular arithmetics:
E Q N V Z ciphertext iv (East) xvi (Q) 13 (Northward) 21 (V) 25 (Z) ciphertext − 23 (Ten) 12 (M) two (C) ten (One thousand) 11 (L) key = −nineteen 4 11 11 14 ciphertext – cardinal = 7 (h) iv (e) eleven (fifty) xi (l) xiv (o) ciphertext – key (mod 26) h eastward l l o → message
Like to the above, if a number is negative, then 26 is added to make the number zero or college.
Thus Bob recovers Alice's plaintext, the message hello. Both Alice and Bob destroy the key sheet immediately after utilize, thus preventing reuse and an attack against the cipher. The KGB often issued its agents old pads printed on tiny sheets of flash paper, newspaper chemically converted to nitrocellulose, which burns almost instantly and leaves no ash.[15]
The classical ane-fourth dimension pad of espionage used actual pads of minuscule, easily concealed paper, a sharp pencil, and some mental arithmetics. The method tin can exist implemented at present as a software program, using data files as input (plaintext), output (ciphertext) and fundamental material (the required random sequence). The exclusive or (XOR) operation is often used to combine the plaintext and the primal elements, and is particularly attractive on computers since it is usually a native machine instruction and is therefore very fast. Information technology is, withal, difficult to ensure that the key textile is actually random, is used simply once, never becomes known to the opposition, and is completely destroyed later on use. The auxiliary parts of a software onetime pad implementation nowadays existent challenges: secure handling/transmission of plaintext, truly random keys, and onetime-merely use of the key.
Attempt at cryptanalysis [edit]
To continue the example from in a higher place, suppose Eve intercepts Alice'due south ciphertext: EQNVZ. If Eve had infinite time, she would find that the key XMCKL would produce the plaintext hello, but she would also find that the key TQURI would produce the plaintext afterward, an equally plausible message:
4 (East) sixteen (Q) thirteen (N) 21 (V) 25 (Z) ciphertext − 19 (T) 16 (Q) 20 (U) 17 (R) 8 (I) possible fundamental = −xv 0 −7 iv 17 ciphertext-key = 11 (50) 0 (a) 19 (t) four (eastward) 17 (r) ciphertext-cardinal (modernistic 26)
In fact, it is possible to "decrypt" out of the ciphertext any message whatsoever with the aforementioned number of characters, simply by using a different key, and in that location is no data in the ciphertext that will allow Eve to choose amongst the various possible readings of the ciphertext.
If the key is non truly random, it is possible to employ statistical analysis to decide which of the plausible keys is the "least" random and therefore more likely to be the correct one. If a key is reused, it will noticeably be the only central that produces sensible plaintexts from both ciphertexts (the chances of some random incorrect key also producing two sensible plaintexts are very slim).
Perfect secrecy [edit]
1-time pads are "data-theoretically secure" in that the encrypted message (i.e., the ciphertext) provides no information about the original message to a cryptanalyst (except the maximum possible length[16] of the message). This is a very stiff notion of security first developed during WWII by Claude Shannon and proved, mathematically, to exist true for the i-time pad by Shannon about the aforementioned time. His result was published in the Bong Arrangement Technical Journal in 1949.[17] Properly used, one-time pads are secure in this sense even against adversaries with space computational power.
Claude Shannon proved, using information theory considerations, that the one-fourth dimension pad has a property he termed perfect secrecy; that is, the ciphertext C gives absolutely no additional information almost the plaintext.[note i] This is considering, given a truly random key that is used but once, a ciphertext tin be translated into whatsoever plaintext of the same length, and all are equally probable. Thus, the a priori probability of a plaintext message M is the aforementioned as the a posteriori probability of a plaintext message M given the respective ciphertext.
Mathematically, this is expressed equally , where is the information entropy of the plaintext and is the provisional entropy of the plaintext given the ciphertext C. (Here, Η is the capital Greek letter eta.) This implies that for every message M and corresponding ciphertext C, there must exist at least one central K that binds them as a one-time pad. Mathematically speaking, this means , where denotes the distinct quantity of keys, ciphers and messages. In other words, if you need to be able to go from any plaintext in message space M to any cipher in cipher-space C (encryption) and from any goose egg in cipher-space C to a plain text in message infinite Yard (decryption), you need at least keys (all keys used with equal probability of to ensure perfect secrecy).
Another manner of stating perfect secrecy is based on the idea that for all messages in bulletin space G, and for all ciphers c in aught space C, nosotros accept , where represents the probabilities, taken over a pick of in key infinite over the coin tosses of a probabilistic algorithm, . Perfect secrecy is a strong notion of cryptanalytic difficulty.[3]
Conventional symmetric encryption algorithms utilize complex patterns of substitution and transpositions. For the all-time of these currently in use, information technology is non known whether there can be a cryptanalytic procedure that can opposite (or, usefully, partially opposite) these transformations without knowing the key used during encryption. Disproportionate encryption algorithms depend on mathematical problems that are thought to be difficult to solve, such as integer factorization and discrete logarithms. However, there is no proof that these problems are hard, and a mathematical breakthrough could make existing systems vulnerable to attack.[note 2]
Given perfect secrecy, in contrast to conventional symmetric encryption, OTP is immune fifty-fifty to brute-strength attacks. Trying all keys simply yields all plaintexts, all equally likely to exist the actual plaintext. Even with known plaintext, like role of the message existence known, brute-forcefulness attacks cannot be used, since an attacker is unable to gain any information about the parts of the key needed to decrypt the residual of the message. The parts that are known will reveal but the parts of the key corresponding to them, and they correspond on a strictly ane-to-ane basis; no part of the key is dependent on any other part.
Quantum computers take been shown by Peter Shor and others to be much faster at solving some of the difficult problems that grant some disproportionate encryption its security. If quantum computers are congenital with plenty qubits, and overcoming some limitations to mistake-correction, some public key cryptography algorithms will get obsolete. Ane-fourth dimension pads, however, will remain secure. Run into quantum cryptography and postal service-breakthrough cryptography for farther word of the ramifications of quantum computers to data security.
Problems [edit]
Despite Shannon's proof of its security, the i-fourth dimension pad has serious drawbacks in practise because it requires:
- Truly random, equally opposed to pseudorandom, one-time pad values, which is a not-lilliputian requirement. See pseudorandom number generator and random number generation.
- True random number generators exist, only are typically slower and more specialized.
- Secure generation and commutation of the former pad values, which must exist at least every bit long as the message.
- The security of the one-fourth dimension pad is just equally secure every bit the security of the one-time pad commutation, because if an attacker is able to intercept the one-time pad value and know it is a one-time pad, they can decrypt the one-time pad'south message.
- Conscientious treatment to brand sure that the ane-time pad values continue to remain cloak-and-dagger and are disposed of correctly, preventing any reuse in whole or in function—hence "ane-time". See information remanence for a word of difficulties in completely erasing computer media.
One-time pads solve few current applied problems in cryptography. High quality ciphers are widely bachelor and their security is not considered a major worry at nowadays.[18] Such ciphers are nigh e'er easier to use than i-time pads; the amount of cardinal material that must be properly and deeply generated, securely distributed and securely stored is far smaller, and public fundamental cryptography overcomes this problem.[19]
True randomness [edit]
High-quality random numbers are difficult to generate. The random number generation functions in most programming language libraries are not suitable for cryptographic use. Even those generators that are suitable for normal cryptographic use, including /dev/random and many hardware random number generators, may make some use of cryptographic functions whose security has not been proven. An example of how true randomness can be achieved is by measuring radioactive emissions.[20]
In particular, one-time apply is absolutely necessary. If a one-time pad is used just twice, simple mathematical operations can reduce it to a running key cipher. For case, if and represent two distinct plaintext messages and they are each encrypted by a common key , then the respective ciphertexts are given by:
where ways XOR. If an attacker were to take both ciphertexts and , then simply taking the XOR of and yields the XOR of the two plaintexts . (This is because taking the XOR of the mutual key with itself yields a abiding bitstream of zeros.) is then the equivalent of a running primal cipher.
If both plaintexts are in a natural language (due east.yard., English language or Russian) then, even though both are underground, each stands a very high take chances of beingness recovered by heuristic cryptanalysis, with possibly a few ambiguities. Of course, a longer message can only be cleaved for the portion that overlaps a shorter message, plus perchance a piddling more by completing a word or phrase. The most famous exploit of this vulnerability occurred with the Venona project.[21]
Primal distribution [edit]
Because the pad, like all shared secrets, must be passed and kept secure, and the pad has to be at least as long every bit the bulletin, at that place is often no point in using one-time padding, equally i can simply send the evidently text instead of the pad (as both tin can exist the same size and accept to be sent deeply). Even so, once a very long pad has been securely sent (e.thou., a computer disk full of random information), information technology tin can be used for numerous future messages, until the sum of their sizes equals the size of the pad. Quantum key distribution too proposes a solution to this trouble, assuming mistake-tolerant breakthrough computers.
Distributing very long i-time pad keys is inconvenient and commonly poses a significant security take a chance.[1] The pad is essentially the encryption key, but dissimilar keys for modernistic ciphers, it must be extremely long and is much too difficult for humans to remember. Storage media such every bit thumb drives, DVD-Rs or personal digital audio players can be used to carry a very large old-pad from place to place in a non-suspicious style, only even so the need to transport the pad physically is a burden compared to the primal negotiation protocols of a mod public-fundamental cryptosystem, and such media cannot reliably be erased securely by any ways short of physical devastation (e.one thousand., incineration). A 4.7 GB DVD-R full of old-pad data, if shredded into particles one mm2 (0.0016 sq in) in size, leaves over 4 megabits of (admittedly hard to recover, only not impossibly and then) data on each particle.[ citation needed ] In addition, the gamble of compromise during transit (for example, a pickpocket swiping, copying and replacing the pad) is probable to exist much greater in practice than the likelihood of compromise for a cipher such as AES. Finally, the endeavor needed to manage quondam pad key material scales very badly for big networks of communicants—the number of pads required goes up every bit the square of the number of users freely exchanging messages. For communication between merely two persons, or a star network topology, this is less of a problem.
The key material must be deeply disposed of after use, to ensure the fundamental fabric is never reused and to protect the letters sent.[i] Because the key textile must exist transported from one endpoint to another, and persist until the bulletin is sent or received, it tin can be more vulnerable to forensic recovery than the transient plaintext it protects (see information remanence).
Authentication [edit]
As traditionally used, i-time pads provide no message authentication, the lack of which can pose a security threat in real-world systems. For example, an attacker who knows that the message contains "run into jane and me tomorrow at three thirty pm" tin can derive the corresponding codes of the pad directly from the two known elements (the encrypted text and the known plaintext). The attacker can and so replace that text by whatever other text of exactly the same length, such as "iii thirty coming together is canceled, stay abode". The attacker'south knowledge of the one-time pad is express to this byte length, which must be maintained for whatever other content of the message to remain valid. This is a little unlike from malleability[22] where it is not taken necessarily that the plaintext is known. Meet too stream cipher assault.
Standard techniques to prevent this, such as the use of a message authentication code tin exist used forth with a one-time pad system to foreclose such attacks, as tin classical methods such as variable length padding and Russian copulation, just they all lack the perfect security the OTP itself has. Universal hashing provides a manner to authenticate messages upwards to an capricious security bound (i.e., for any p > 0, a large enough hash ensures that even a computationally unbounded attacker's likelihood of successful forgery is less than p), but this uses additional random data from the pad, and removes the possibility of implementing the organization without a reckoner.
Common implementation errors [edit]
Due to its relative simplicity of implementation, and due to its promise of perfect secrecy, 1-time-pad enjoys loftier popularity among students learning about cryptography, particularly as its ofttimes the very first algorithm to exist presented and implemented during a course. Unfortunately the implementations oft suspension the requirements for data theoretical security in one or more ways:
- The pad is generated via some algorithm, that expands i or more small values into a longer "quondam-pad". This applies equally to all algorithms, from completely insecure basic mathematical operations like square root decimal expansions, to complex, cryptographically secure pseudo-random random number generators (CSPRNGs). None of these implementations are one-time-pads, but stream ciphers by definition. All erstwhile pads must be generated by a not-algorithmic process, e.g. by a hardware random number generator.
- The pad is exchanged using non-information-theoretically secure methods. If the one-time-pad is encrypted with not-information theoretically secure algorithm for delivery, the security of the cryptosystem is only as secure every bit the weakest link of the cryptosystem. A common wrong delivery mechanism for one-fourth dimension-pad is a standard hybrid cryptosystem that relies on symmetric key cryptography for pad encryption, and asymmetric cryptography for symmetric central delivery. The correct methods for one-fourth dimension pad delivery are primarily quantum key distribution, a sneakernet or courier service, or a dead drop.
- The implementation does not feature an unconditionally secure authentication mechanism such equally a One-time MAC.
- The pad is reused (see Venona projection)
- The pad is non destroyed immediately afterward employ.
Uses [edit]
Applicability [edit]
Despite its problems, the 1-time-pad retains some practical involvement. In some hypothetical espionage situations, the one-fourth dimension pad might exist useful because it tin can be computed by hand with only pencil and paper. Indeed, about all other loftier quality ciphers are entirely impractical without computers. In the modern world, yet, computers (such as those embedded in personal electronic devices such equally mobile phones) are and so ubiquitous that possessing a computer suitable for performing conventional encryption (for instance, a telephone that can run concealed cryptographic software) will commonly not attract suspicion.
- The one-time-pad is the optimum cryptosystem with theoretically perfect secrecy.
- The old-pad is 1 of the nearly practical methods of encryption where one or both parties must practise all piece of work by hand, without the aid of a estimator. This fabricated information technology of import in the pre-computer era, and it could conceivably nonetheless be useful in situations where possession of a reckoner is illegal or incriminating or where trustworthy computers are non bachelor.
- I-time pads are practical in situations where ii parties in a secure environment must be able to depart from one some other and communicate from 2 split secure environments with perfect secrecy.
- The 1-fourth dimension-pad can exist used in superencryption.[23]
- The algorithm most commonly associated with quantum central distribution is the quondam pad.
- The one-time pad is mimicked by stream ciphers.
- The erstwhile pad can exist a office of an introduction to cryptography.[24]
Historical uses [edit]
One-time pads accept been used in special circumstances since the early 1900s. In 1923, information technology was employed for diplomatic communications past the High german diplomatic institution.[25] The Weimar Democracy Diplomatic Service began using the method in about 1920. The breaking of poor Soviet cryptography by the British, with letters made public for political reasons in two instances in the 1920s (ARCOS case), appear to have induced the Soviet Union to adopt one-time pads for some purposes by effectually 1930. KGB spies are also known to have used pencil and newspaper one-fourth dimension pads more than recently. Examples include Colonel Rudolf Abel, who was arrested and convicted in New York City in the 1950s, and the 'Krogers' (i.e., Morris and Lona Cohen), who were arrested and convicted of espionage in the United Kingdom in the early 1960s. Both were plant with concrete one-fourth dimension pads in their possession.
A number of nations have used i-fourth dimension pad systems for their sensitive traffic. Leo Marks reports that the British Special Operations Executive used onetime pads in World War 2 to encode traffic betwixt its offices. 1-fourth dimension pads for employ with its overseas agents were introduced late in the war.[thirteen] A few British ane-time tape cipher machines include the Rockex and Noreen. The German Stasi Sprach Machine was likewise capable of using 1 fourth dimension tape that East Germany, Russia, and fifty-fifty Cuba used to transport encrypted messages to their agents.[26]
The Globe War Ii vocalism scrambler SIGSALY was also a form of 1-fourth dimension system. It added noise to the signal at one finish and removed it at the other finish. The noise was distributed to the channel ends in the form of large shellac records that were manufactured in unique pairs. In that location were both starting synchronization and longer-term phase drift issues that arose and were solved before the system could be used.
The hotline betwixt Moscow and Washington D.C., established in 1963 later the 1962 Cuban Missile Crisis, used teleprinters protected by a commercial onetime tape organization. Each state prepared the keying tapes used to encode its messages and delivered them via their diplomatic mission in the other country. A unique reward of the OTP in this instance was that neither land had to reveal more sensitive encryption methods to the other.[27]
U.Southward. Army Special Forces used former pads in Vietnam. By using Morse code with one-time pads and continuous moving ridge radio manual (the carrier for Morse lawmaking), they accomplished both secrecy and reliable communications.[28]
During the 1983 Invasion of Grenada, U.S. forces found a supply of pairs of one-time pad books in a Cuban warehouse.[29]
Starting in 1988, the African National Congress (ANC) used disk-based ane-time pads every bit function of a secure advice arrangement between ANC leaders outside S Africa and in-country operatives as part of Operation Vula,[30] a successful effort to build a resistance network within S Africa. Random numbers on the disk were erased subsequently utilize. A Belgian airline stewardess acted as courier to bring in the pad disks. A regular resupply of new disks was needed every bit they were used up fairly apace. 1 problem with the system was that information technology could non be used for secure information storage. Later Vula added a stream cipher keyed by book codes to solve this problem.[31]
A related notion is the i-time lawmaking—a point, used only once; e.one thousand., "Alpha" for "mission completed", "Bravo" for "mission failed" or even "Torch" for "Allied invasion of French Northern Africa"[32] cannot be "decrypted" in any reasonable sense of the word. Understanding the message will require boosted information, often 'depth' of repetition, or some traffic analysis. However, such strategies (though often used by real operatives, and baseball game coaches)[ commendation needed ] are not a cryptographic one-time pad in any significant sense.
NSA [edit]
At least into the 1970s, the U.Due south. National Security Agency (NSA) produced a diversity of transmission 1-time pads, both general purpose and specialized, with 86,000 one-fourth dimension pads produced in financial year 1972. Special purpose pads were produced for what NSA called "pro forma" systems, where "the bones framework, class or format of every bulletin text is identical or nearly so; the same kind of information, bulletin after message, is to be presented in the same club, and simply specific values, like numbers, change with each message." Examples included nuclear launch messages and radio direction finding reports (COMUS).[33] : pp. 16–18
General purpose pads were produced in several formats, a simple listing of random letters (DIANA) or just numbers (CALYPSO), tiny pads for covert agents (MICKEY MOUSE), and pads designed for more rapid encoding of short messages, at the cost of lower density. One instance, ORION, had 50 rows of plaintext alphabets on one side and the corresponding random nix text letters on the other side. By placing a sail on top of a slice of carbon paper with the carbon confront upward, one could circle one letter in each row on one side and the corresponding letter on the other side would be circled by the carbon newspaper. Thus one ORION sheet could apace encode or decode a message upward to 50 characters long. Production of ORION pads required printing both sides in exact registration, a hard procedure, so NSA switched to some other pad format, MEDEA, with 25 rows of paired alphabets and random characters. (See Eatables:Category:NSA 1-time pads for illustrations.)
The NSA also built automated systems for the "centralized headquarters of CIA and Special Forces units and so that they can efficiently procedure the many separate former pad messages to and from private pad holders in the field".[33] : pp. 21–26
During World War II and into the 1950s, the U.Due south. made extensive employ of onetime tape systems. In addition to providing confidentiality, circuits secured by one-fourth dimension tape ran continually, even when there was no traffic, thus protecting against traffic analysis. In 1955, NSA produced some one,660,000 rolls of one time tape. Each roll was viii inches in diameter, contained 100,000 characters, lasted 166 minutes and cost $4.55 to produce. By 1972, only 55,000 rolls were produced, equally erstwhile tapes were replaced past rotor machines such as SIGTOT, and afterward by electronic devices based on shift registers.[33] : pp. 39–44 The NSA describes one-time record systems like 5-UCO and SIGTOT equally being used for intelligence traffic until the introduction of the electronic cipher based KW-26 in 1957.[34]
Exploits [edit]
While one-time pads provide perfect secrecy if generated and used properly, modest mistakes can lead to successful cryptanalysis:
- In 1944–1945, the U.Due south. Army'due south Signals Intelligence Service was able to solve a one-fourth dimension pad organisation used by the German language Foreign Office for its high-level traffic, codenamed GEE.[35] GEE was insecure considering the pads were not sufficiently random—the car used to generate the pads produced predictable output.
- In 1945, the United states of america discovered that Canberra–Moscow letters were being encrypted first using a code-book and and then using a one-fourth dimension pad. However, the former pad used was the aforementioned i used by Moscow for Washington, D.C.–Moscow messages. Combined with the fact that some of the Canberra–Moscow messages included known British government documents, this allowed some of the encrypted letters to exist broken.[ citation needed ]
- Quondam pads were employed past Soviet espionage agencies for covert communications with agents and amanuensis controllers. Analysis has shown that these pads were generated by typists using actual typewriters. This method is of course not truly random, as information technology makes certain user-friendly fundamental sequences more likely than others, yet it proved to be more often than not effective considering while a person will not produce truly random sequences they equally do non follow the same kind of structured mathematical rules that a machine would either, and each person generates ciphers in a different way making attacking any bulletin challenging. Without copies of the key cloth used, only some defect in the generation method or reuse of keys offered much hope of cryptanalysis. Commencement in the late 1940s, United states of america and UK intelligence agencies were able to interruption some of the Soviet one-time pad traffic to Moscow during WWII as a result of errors made in generating and distributing the key textile. 1 proffer is that Moscow Eye personnel were somewhat rushed by the presence of German troops simply exterior Moscow in late 1941 and early 1942, and they produced more than one copy of the same key material during that period. This decades-long endeavor was finally codenamed VENONA (Helpmate had been an earlier proper name); it produced a considerable amount of information. Fifty-fifty so, only a pocket-size percentage of the intercepted messages were either fully or partially decrypted (a few chiliad out of several hundred grand).[36]
- The 1-fourth dimension tape systems used by the U.S. employed electromechanical mixers to combine bits from the bulletin and the 1-fourth dimension record. These mixers radiated considerable electromagnetic free energy that could be picked up by an adversary at some altitude from the encryption equipment. This issue, first noticed past Bell Labs during World War Two, could allow interception and recovery of the plaintext of messages existence transmitted, a vulnerability code-named Tempest.[33] : pp. 89 ff
See also [edit]
- Agrippa (A Book of the Expressionless)
- Data theoretic security
- Numbers station
- Former countersign
- Session key
- Steganography
- Tradecraft
- Unicity distance
Notes [edit]
- ^ That is to say, the "information proceeds" or Kullback–Leibler departure of the plaintext message from the cyphertext message is zero.
- ^ Most asymmetric encryption algorithms rely on the facts that the best known algorithms for prime factorization and computing discrete logarithms are superpolynomial fourth dimension. At that place is a strong belief that these problems are not solvable past a Turing machine in time that scales polynomially with input length, rendering them difficult (hopefully, prohibitively and then) to be cleaved via cryptographic attacks. Nevertheless, this has non been proven.
References [edit]
- ^ a b c "Intro to Numbers Stations". Archived from the original on 18 Oct 2014. Retrieved 13 September 2014.
- ^ "Former Pad (OTP)". Cryptomuseum.com. Archived from the original on 2014-03-14. Retrieved 2014-03-17 .
- ^ a b c Shannon, Claude (1949). "Communication Theory of Secrecy Systems" (PDF). Bong System Technical Journal. 28 (4): 656–715. doi:10.1002/j.1538-7305.1949.tb00928.10.
- ^ Miller, Frank (1882). Telegraphic code to insure privacy and secrecy in the transmission of telegrams. C.M. Cornwell.
- ^ a b Bellovin, Steven M. (2011). "Frank Miller: Inventor of the One-Fourth dimension Pad". Cryptologia. 35 (3): 203–222. doi:x.1080/01611194.2011.583711. ISSN 0161-1194. S2CID 35541360.
- ^ "'Surreptitious signaling organisation patent' on Google.Com". google.com. Archived from the original on 11 March 2016. Retrieved 3 February 2016.
- ^ Kahn, David (1996). The Codebreakers. Macmillan. pp. 397–8. ISBN978-0-684-83130-5.
- ^ "Ane-Time-Pad (Vernam's Cipher) Frequently Asked Questions, with photo". Archived from the original on 2006-05-07. Retrieved 2006-05-12 .
- ^ Savory, Stuart (2001). "Chiffriergerätebau : 1-Fourth dimension-Pad, with photo" (in German). Archived from the original on 2011-05-30. Retrieved 2006-07-24 .
- ^ a b c Kahn, David (1967). The Codebreakers. Macmillan. pp. 398 ff. ISBN978-0-684-83130-5.
- ^ John Markoff (July 25, 2011). "Codebook Shows an Encryption Form Dates Back to Telegraphs". The New York Times. Archived from the original on May 21, 2013. Retrieved 2011-07-26 .
- ^ Peng, Weiping; Cui, Shuang; Vocal, Cheng (2021-01-20). Raja, Gulistan (ed.). "One-time-pad cipher algorithm based on confusion mapping and Dna storage technology". PLOS I. sixteen (i): e0245506. Bibcode:2021PLoSO..1645506P. doi:10.1371/journal.pone.0245506. ISSN 1932-6203. PMC7817086. PMID 33471849.
- ^ a b Marks, Leo (1998). Between Silk and Cyanide: a Codemaker'southward Story, 1941-1945. HarperCollins. ISBN978-0-684-86780-9.
- ^ Sergei N Molotkov (Institute of Solid-State Physics, Russian Academy of Sciences, Chernogolovka, Moscow region, Russian Federation) (22 Feb 2006). "Quantum cryptography and 5 A Kotel'nikov's ane-fourth dimension cardinal and sampling theorems". Physics-Uspekhi. 49 (seven): 750–761. Bibcode:2006PhyU...49..750M. doi:10.1070/PU2006v049n07ABEH006050. Retrieved 2009-05-03 .
{{cite journal}}: CS1 maint: multiple names: authors listing (link) PACS numbers: 01.x.Fv, 03.67.Dd, 89.70.+c and openly in Russian Квантовая криптография и теоремы В.А. Котельникова об одноразовых ключах и об отсчетах. УФН - ^ Robert Wallace and H. Keith Melton, with Henry R. Schlesinger (2008). Spycraft: The Secret History of the CIA's Spytechs, from Communism to al-Qaeda. New York: Dutton. p. 452. ISBN978-0-525-94980-0.
- ^ The actual length of a plaintext message tin can hidden by the addition of inapplicable parts, called padding. For instance, a 21-graphic symbol ciphertext could conceal a 5-grapheme message with some padding convention (east.g. "-PADDING- Hello -XYZ-") as much equally an actual 21-character message: an observer can thus only deduce the maximum possible length of the pregnant text, non its exact length.
- ^ Shannon, Claude Due east. (October 1949). "Communication Theory of Secrecy Systems" (PDF). Bell Organisation Technical Journal. 28 (4): 656–715. doi:10.1002/j.1538-7305.1949.tb00928.x. hdl:10338.dmlcz/119717. Archived from the original (PDF) on 2012-01-xx. Retrieved 2011-12-21 .
- ^ Lars R. Knudsen & Matthew Robshaw (2011). The Block Cipher Companion. Springer Science & Concern Media. pp. ane–fourteen. ISBN9783642173424 . Retrieved 26 July 2017.
- ^ Schneier, Bruce. "One-Fourth dimension Pads". Archived from the original on 2005-04-03.
- ^ Singh, Simon (2000). The Lawmaking Book. United States: Ballast Books. pp. 123. ISBN978-0-385-49532-5.
- ^ "The Translations and KGB Cryptographic Systems" (PDF). The Venona Story. Fort Meade, Maryland: National Security Bureau. 2004-01-15. pp. 26–27 (28–29th of 63 in PDF). Archived from the original (PDF) on 2009-05-10. Retrieved 2009-05-03 .
KGB's cryptographic fabric manufacturing eye in the Soviet Union apparently reused some of the pages from one-fourth dimension pads. This provided Arlington Hall with an opening.
- ^ Safavi-Naini, Reihaneh (22 July 2008). Information Theoretic Security: 3rd International Conference, ICITS 2008, Calgary, Canada, Baronial 10-thirteen, 2008, Proceedings. Springer Scientific discipline & Concern Media. ISBN9783540850922 – via Google Books.
- ^ A "way to combine multiple block algorithms" and so that "a cryptanalyst must break both algorithms" in §fifteen.viii of Applied Cryptography, Second Edition: Protocols, Algorithms, and Source Code in C by Bruce Schneier. Wiley Computer Publishing, John Wiley & Sons, Inc.
- ^ Introduction to modern cryptography, J Katz, Y Lindell, 2008.
- ^ Kahn, David (1996). The Codebreakers. Macmillan. pp. 402–3. ISBN978-0-684-83130-5.
- ^ "Stasi Sprach Morse Auto". The Numbers Stations Inquiry and Information Center. Archived from the original on March thirteen, 2015. Retrieved March one, 2015.
- ^ Kahn. The Codebreakers. p. 715.
- ^ Hieu, Phan Duong (April 2007). "Cryptology during the French and American Wars in Vietnam" (PDF). Cryptologia. 41 (6): one–21. doi:10.1080/01611194.2017.1292825. S2CID 3780267. Retrieved xiv April 2020.
- ^ [ dead link ] http://www.seas.harvard.edu/courses/emr12/iv.pdf folio 91 [ expressionless link ]
- ^ "Functioning Vula: a secret Dutch network confronting apartheid", Radio Netherlands Archives, September 9, 1999
- ^ Jenkin, Tim (May–October 1995). "Talking to Vula: The Story of the Secret Clandestine Communications Network of Operation Vula". Mayibuye. Archived from the original on 2014-08-26. Retrieved 24 Baronial 2014.
Our system was based on the erstwhile pad, though instead of having paper pads the random numbers were on a disk.
- ^ Pidgeon, Geoffrey (2003). "Chapter 28: Bill Miller – Tea with the Germans". The Secret Wireless State of war – The story of MI6 Communications 1939-1945. UPSO Ltd. p. 249. ISBN978-1-84375-252-three.
- ^ a b c d Boak, David G. (July 1973) [1966]. A History of U.Southward. Communications Security; the David 1000. Boak Lectures, Vol. I (PDF) (2015 declassification review ed.). Ft. George Thou. Meade, MD: U.S. National Security Agency. Archived from the original (PDF) on 2017-05-25. Retrieved 2017-04-23 .
- ^ Klein, Melville (2003). "Securing Tape Communications: The TSEC/KW-26" (PDF). NSA. Archived from the original (PDF) on 2006-02-xiii. Retrieved 2006-05-12 .
- ^ Erskine, Ralph, "Enigma'south Security: What the Germans Really Knew", in Activeness this Day, edited by Ralph Erskine and Michael Smith, pp. 370–386, 2001.
- ^ "The Venona Translations" (PDF). The Venona Story. Fort Meade, Maryland: National Security Agency. 2004-01-15. p. 17th (of 63 in PDF) merely marked xv. Archived from the original (PDF) on 2009-05-10. Retrieved 2009-05-03 .
Arlington Hall's ability to read the VENONA messages was spotty, being a role of the underlying code, primal changes, and the lack of volume. Of the bulletin traffic from the KGB New York function to Moscow, 49 percent of the 1944 letters and xv percent of the 1943 messages were readable, simply this was true of only 1.8 percent of the 1942 messages. For the 1945 KGB Washington office to Moscow messages, only 1.5 percent were readable. About 50 percent of the 1943 GRU-Naval Washington to Moscow/Moscow to Washington messages were read but none from whatsoever other year.
Further reading [edit]
- Rubina, Frank (1996). "One-Fourth dimension Pad cryptography". Cryptologia. 20 (four): 359–364. doi:10.1080/0161-119691885040. ISSN 0161-1194.
- Fostera, Caxton C. (1997). "Drawbacks of the One-fourth dimension Pad". Cryptologia. 21 (4): 350–352. doi:10.1080/0161-119791885986. ISSN 0161-1194.
External links [edit]
- Detailed clarification and history of One-fourth dimension Pad with examples and images on Cipher Machines and Cryptology
- The FreeS/WAN glossary entry with a discussion of OTP weaknesses
Source: https://en.wikipedia.org/wiki/One-time_pad








![{\displaystyle {\underset {k\Leftarrow \mathrm {K} }{\operatorname {Pr} }}[E_{k}(m_{1})=c]={\underset {k\Leftarrow \mathrm {K} }{\operatorname {Pr} }}[E_{k}(m_{2})=c]}](https://wikimedia.org/api/rest_v1/media/math/render/svg/478ed9b5381e6ca266eb4349e8b305cdeb56d2bc)












0 Response to "What Is the Probability That the Correct Source Element Can Be Selected by an Adversary on One Try?"
Post a Comment